wordpress-accessible-wpconfig
Context
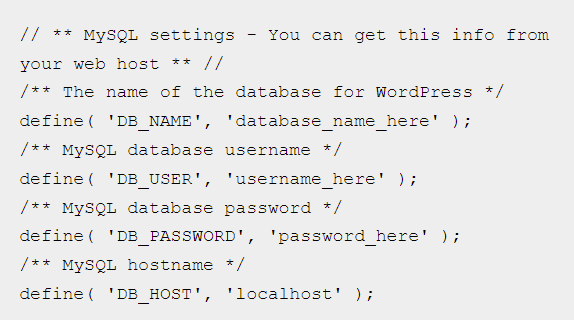
The wp-config file is one of the most important files in your WordPress installation. This configuration file may contain details such as database connection information.
Such file should never be deployed in production as it contains at least development secrets which are potentially reused in production.
Impacted Assets
In the scenario the concerned database is accessible to the attacker, confidentiality and integrity of the data stored may be compromised.
Exploit or command to run
There is no command to run, wp-config file is usually located in https://wordpress-path/wp-config.php.
In the scenario there is apublicly exposed database, stored data will be accessed and potentially modified by the attacker, which will lead to direct and indirect financial losses.
Remediation
The only solution is restricting access to the file. As detailed in the link https://www.getastra.com/blog/911/secure-wp-config-file/, you should, for an apache server:
- Open the .htaccess file using any text editor application
- Include the following lines of code in the end of the .htaccess file:
# Deny access to wp-config/php
<Files wp-config.php>
Order allow,deny
Deny from all
</Files>
For other related application server as for example nginx, see configuration file manual, for example in nginx configuration file located in /usr/local/nginx/conf (Unix server).
/location ~ /(wp-config.php) {
deny all;
return 404;
}
...