Password authentication enabled
Context
SSH is an administration protocol used to grant access to the server hosting the protocol.
Administrators use SSH for updates, maintenance and general security tasks.
To connect to the server through SSH, the protocol offers 2 ways of authentication:
Combination of user / password
Use of cryptographic key
As such, cryptographic keys cannot be guessed by an attacker as the file is complex and long. However, when authentication through password is enabled, users may use weak or default password to login to the system, which can be guessed by the attacker through bruteforce attacks.
Impacted Assets
The underlying server hosting the SSH protocol.
In the case the attacker manages to guess a password and take control of the server, the impact can lead to lateral propagation on connected assets depending on security configuration.
Exploit or command to run
SSH protocol bruteforce script is easy to develop. Hard part is to guess the combination of user / password.
Root account is often present in the system and gives administration rights on the system. As such, it is the primary target of attackers.
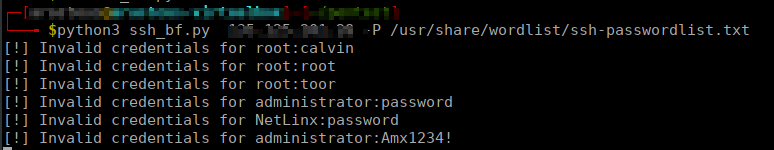
The image belows shows our script trying various combination of default password on the protocol. Dedicated attacker can try various possibilities until the login is successful.
Consequences
Cyber-terms
In the scenario the attacker obtain valid credentials, direct access on the server would be granted that could lead to direct impact on the confidentiality, integrity, disponibility and potentially tracability of the data stored in the server.
Managerial terms
Exploitation of the vulnerability leads to direct financiary losses by impacting disponibility and integrity of server assets and needed post investigation by security experts to assert connected assets have not been impacted.
Remediation
Short-term action
In the case the server is hosted and managed by your company, we recommend as a short-term action to add fail2ban feature on the server: https://www.fail2ban.org/wiki/index.php/Main_Page
The implementation of this mechanism will automatically ban each IP adress that will try 5 failed login attempts.
Such configuration will greatly increase bruteforce complexity for the attacker, but will not reduce the risk to 0.
Mid term Actions
We recommend forcing administrators and developpers the use of RSA public key for authentication and disabling the password authentication method:
Such configuration is not vulnerable to bruteforce attacks.
There is various documentation on the process of generating RSA keys, but official page is detailed and precise on the subject: